MIT researchers have bad news for users of anonymity browser Tor

(matt) on Flickr
Researchers at the Massachusetts Institute of Technology have found a way to identify websites hidden with the Tor anonymity service, the most-respected online anonymity service in the world, with an 88 percent accuracy rate.
That’s big, and bad, news for the 2.5 million or so daily Tor users around the world, who rely on the service for everything from criminal activity to getting around government censorship.
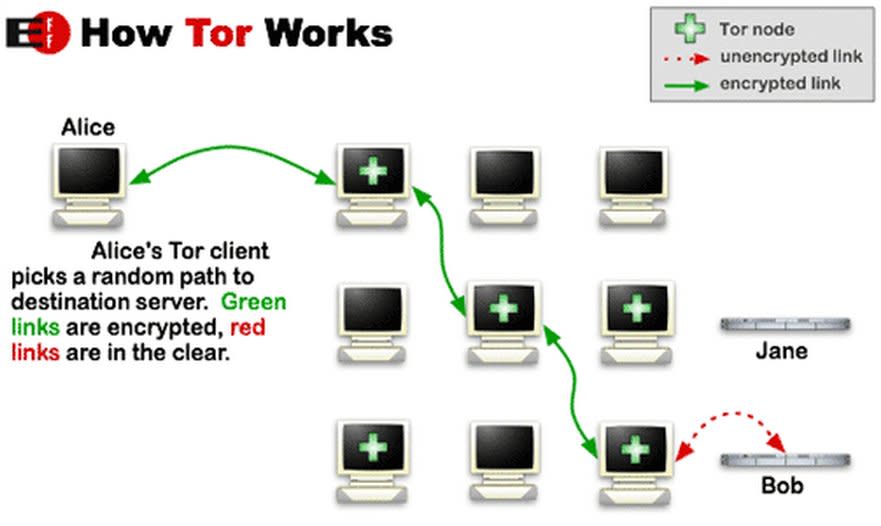
Tor, an acronym for “The Onion Router,” was developed by the U.S. military to let American intelligence sources communicate with Washington freely without the watchful eye of an adversarial government.
Now, since the software has gone public, it has attracted journalists, dissidents, child pornographers andmillions of other Internet users who create websites within Tor’s hidden services section. It’s those hidden services, which shield a site’s IP address and other identifying information, that computer scientists at MIT have unveiled.
The attack works by collecting a vast amount of network data from already known Tor hidden services in advance, assigning a digital fingerprint to each of the services in question.
By following that fingerprint through computer connection points around the world, and analyzing traffic patterns, the team found that those connections could find a hidden service computer’s information 88 percent of the time. They did all of this without breaking Tor’s encryption.
“Our goal is to show that it is possible for a local passive adversary to deanonymize users with hidden services actives without the need to perform end-to-end traffic analysis,” wrote MIT researchers in a new paper with the Qatar Computing Research Institute.
EFF
“We assume that the attacker is able to monitor the traffic between the user and the Tor network. The attacker’s goal is to identify that a user is either operating or connected to a hidden service. In addition, the attacker then aims to identity the hidden service associated with the user.”
The researchers said they have been in contact with Tor’s security team, which plans to institute improved measures.
More from International Business Times:
Greek Stocks Brace For Plunge As Athens Stock Exchange To Reopen For First Time In A Month
Trans-Pacific Partnership: TPP Trade Talks Fall Short Of Deal
This article originally appeared at International Business Times. Copyright 2015. Follow International Business Times on Twitter.
NOW WATCH: How to hide on the internet
The post MIT researchers have bad news for users of anonymity browser Tor appeared first on Business Insider.

 Yahoo Finance
Yahoo Finance 
